In today’s digital age, the security of your business’s IT environment is more critical than ever. Small oversights can lead to major cybersecurity incidents that can jeopardize your company’s data and reputation. Here are five essential tips to keep your IT environment secure:
1️⃣ Use Multi-Factor Authentication (MFA)
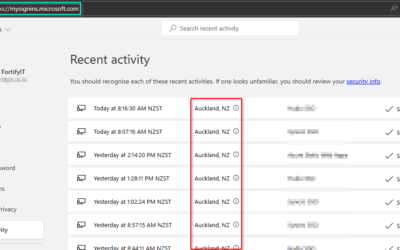
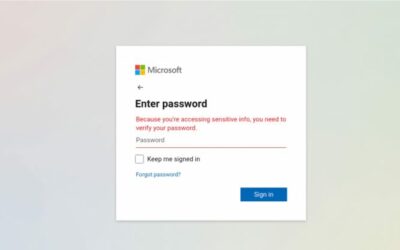
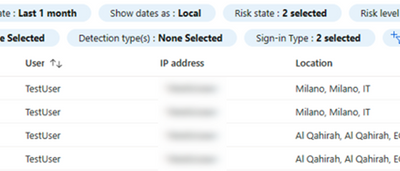
MFA adds an extra layer of security by requiring two or more verification methods—a password, a security token, or even a fingerprint. It’s a simple yet effective way to protect your accounts from unauthorized access.
2️⃣ Regular Software Updates
Outdated software is a prime target for cyberattacks. Ensure that all your software—including your operating system and applications—are up to date with the latest security patches.
3️⃣ Employee Training
Human error is often the weakest link in cybersecurity. Educate your team about the dangers of phishing emails, the importance of strong passwords, and best practices for internet usage.
4️⃣ Back-Up Important Data
Always have a backup of essential data and store it in a secure location, either on a physical drive or cloud storage. Regularly test these backups to ensure that data restoration works when you need it the most.
5️⃣ Use a Firewall
A firewall acts as a barrier between your internal network and incoming traffic from external sources. It helps filter out malicious activity and can prevent unauthorized access to your system.
Remember, IT security is not a one-time effort; it’s an ongoing process that requires vigilance and proactive measures.
If you’re concerned about the security of your IT environment and want expert guidance, feel free to reach out to us. We specialize in Managed IT Support tailored for small and medium-sized businesses in the Auckland area.