Data protection is a necessity for businesses of all sizes. A single data breach can cost your company not just financially but also damage your reputation.
Here are three simple but powerful steps you can take today to fortify your data security.
1. Remove Admin Rights from Staff
Admin rights can be a double-edged sword. While it may seem convenient to let staff handle their computer issues by themselves, this level of access can also expose your network to a host of security threats. From unintentional downloading of malware to accidental changes in systemwide configurations, the risks are not worth it. Instead, keep admin rights restricted to IT personnel who are trained to handle such responsibilities.
2. Maintain an Offsite Backup
The adage ‘don’t put all your eggs in one basket’ applies perfectly here. Keeping all your data in one place makes you vulnerable to catastrophic data loss due to hardware failure, natural disasters, or cyberattacks. Maintain an offsite backup of your important files. This backup should be secure and regularly updated to ensure that you can quickly recover your data if needed.
3. Restrict Data Access
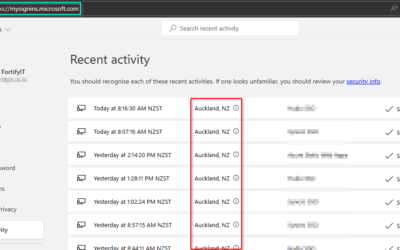
Not everyone in your organization needs access to all your data. Implement a role-based access control system to ensure that employees can only access the data relevant to their job functions. This minimizes the risk of sensitive data falling into the wrong hands and helps to maintain compliance with privacy regulations.
Data security is a complex challenge but starting with these three steps can significantly mitigate risks. If you’re a business in Auckland looking for local, personable IT support to help secure your data, don’t hesitate to reach out. We’re here to help!