For any IT support company, understanding the characteristics of the ideal customer is not just beneficial—it’s essential for long-term success. Here’s our breakdown;
1. Business Size: The SME Sweet Spot
While IT support is important for businesses of all sizes, small and medium-sized enterprises (SMEs) often benefit the most. These businesses are large enough to have complex IT needs but may not have the in-house capabilities to manage them efficiently.
2. Location: Local Businesses in Auckland
For IT support companies based in Auckland, local businesses are a prime focus. Proximity allows for faster and more personalized service, something both parties value.
3. Budget: Willingness to Invest
Businesses that understand the ROI of effective IT support are usually willing to allocate a budget for quality services. They know that skimping on IT can and will lead to more significant costs down the line.
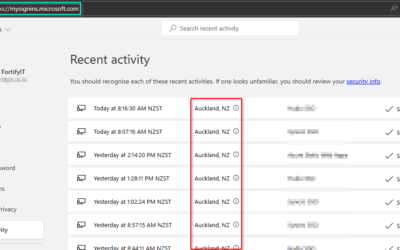
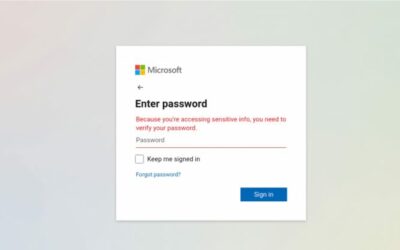
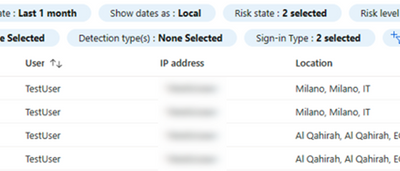
4. Priority on Security
Companies that prioritize data security, recognizing the risks of cyber threats, are a great match for managed IT support services.
5. Attitude: Open to Outsourcing
The ideal customer understands the value of outsourcing specialized tasks. They recognize that their time is better spent focusing on their core business rather than troubleshooting IT issues.
6. Industry: Not Just Tech Companies
Many people assume that only tech companies need IT support. In reality, almost all sectors including healthcare, retail, and manufacturing, finance, property also have complex IT needs and can greatly benefit from specialized support.
Are you one of these people? If you run a business in Auckland, and you align with these characteristics, you might be a fit for our IT support services. Contact me for a quick chat and we can discuss how we can make your business more efficient, secure, and successful.