If you’re running a small or medium-sized business in Auckland, these are the critical conversations you should be having with your IT support provider. Ignoring these could mean the difference between a secure, efficient operation and a costly setback.
1. The Non-Negotiable: Multi-Factor Authentication
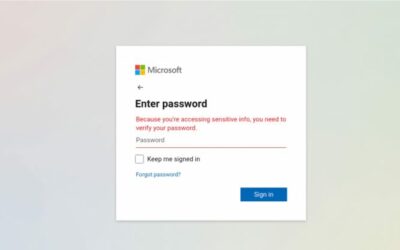
Secure passwords alone aren’t enough anymore. Multi-Factor Authentication (MFA) adds an extra layer of protection and is a free feature already included in Microsoft 365 and G Suite. Discuss enabling this with your IT support ASAP.
2. The Lifesaver: Backup Testing
You may have regular backups, but have you ensured they’re reliable? Backups should be tested at least every month to confirm they’ll work when you most need them. Consult your IT partner to make this a recurring task.
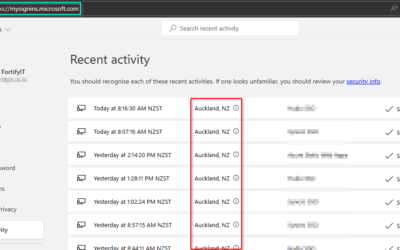
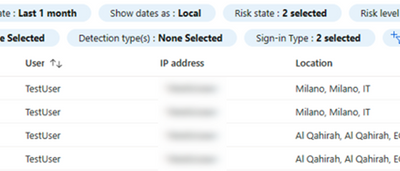
3. The Gatekeeper: Auditing Remote Access and Network Security
With remote work becoming increasingly common, auditing your network’s remote access points is critical. Whether it’s RDP, VPNs, or firewalls, ensure you discuss the current setup and potential vulnerabilities with your IT support. Regularly review who has access and whether your security protocols are up to date.
4. The Watchtower: Software Updates
Neglecting software updates will open the door to cyber threats—it’s not a matter of if, but when. Collaborate with your IT provider to maintain a regular update schedule, so you can focus on running your business without cyber concerns.
5. The Safety Net: Disaster Recovery Plan
Every business needs a comprehensive Disaster Recovery Plan (DRP). Discuss the specifics with your IT support, from data recovery steps to team roles and communication strategies for handling significant IT incidents.
Ready for peace of mind? If you’re looking for a local, personable, and experienced IT partner in Auckland to help you manage these essential points and more, reach out for a free consultation. Make your business as resilient and ambitious as you are.