Email spam is a nuisance we all deal with, but beyond being an annoyance, it can pose real security risks to your business. Here’s how to safeguard against spam and related threats.
Microsoft 365 Policies 🛡️
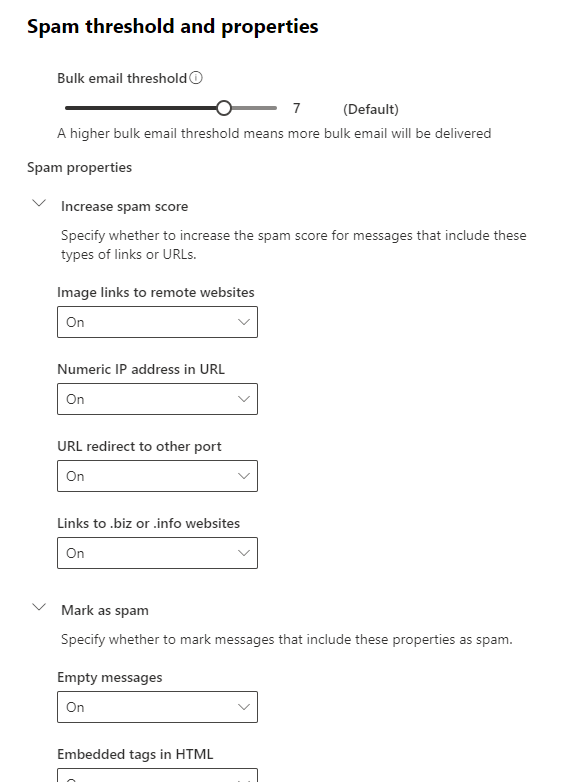
Microsoft 365 provides robust mail flow rules and spam filters. You can configure these policies to filter out known spam email addresses and detect suspicious email content automatically. For businesses in Auckland, our Managed IT Support can help you tailor these policies for your specific needs.
Dedicated Spam Filters 📨
For an added layer of security, consider implementing a dedicated spam filter. These tools use machine learning and real-time threat analysis to filter out spam before it hits your inbox.
Employee Training 📚
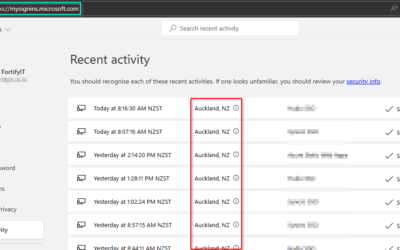
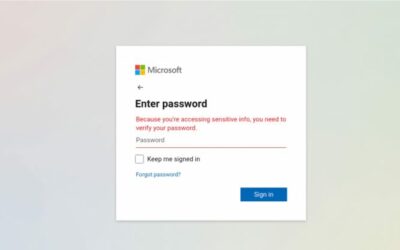
The human factor cannot be overlooked when combating spam. Regular training sessions can educate your team on how to identify phishing emails and misleading links, greatly reducing the risk of a successful cyber attack.
Phishing Simulation 🎣
One of the best ways to test your defenses is through phishing simulation exercises. These mock attacks can be orchestrated to gauge how well your employees are prepared to identify and handle actual phishing attempts.
Key Takeaways 🔑
Combating spam requires a multi-pronged approach that involves both technological solutions and human awareness. It’s not just about filtering emails but also about training your team to recognize and respond to threats effectively.
If spam and cybersecurity are concerns for your business, our specialized Managed IT Support services are here to assist small and medium-sized businesses in Auckland. From setting up email policies to running phishing simulations, we’ve got you covered.
Stay spam-free, Auckland! 📭